Grafana is an open source software to create visualization of time-series data. This can graph AWS CloudWatch Metrics too.
As a security best practice when using Grafana on an EC2 Instance it is recommended to use an IAM Role. Using a credentials file may expose access to your AWS Account if ever other people gain access to your Grafana Server.
Follow the step-by-step instructions below on how to attach an IAM Role to your Grafana EC2 Instance and set Grafana to access CloudWatch.
- Creation of IAM Role for Grafana EC2 Instance
- Adding CloudWatch Data Source
- Testing CloudWatch Data Source
Creation of IAM Role for Grafana EC2 Instance
Create an IAM policy with the below permission in JSON. Name this GrafanaAccessPolicy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowReadingMetricsFromCloudWatch",
"Effect": "Allow",
"Action": [
"cloudwatch:DescribeAlarmsForMetric",
"cloudwatch:ListMetrics",
"cloudwatch:GetMetricStatistics",
"cloudwatch:GetMetricData"
],
"Resource": "*"
},
{
"Sid": "AllowReadingTagsInstancesRegionsFromEC2",
"Effect": "Allow",
"Action": ["ec2:DescribeTags", "ec2:DescribeInstances", "ec2:DescribeRegions"],
"Resource": "*"
},
{
"Sid": "AllowReadingResourcesForTags",
"Effect": "Allow",
"Action": "tag:GetResources",
"Resource": "*"
}
]
}Then create an IAM Role with the following properties.
| Trusted Entity Type | EC2 |
| Policies | GrafanaAccessPolicy |
| Role name | GrafanaAccessRole |
Then attach the GrafanaAccessRole to our Grafana-Server EC2 Instance.
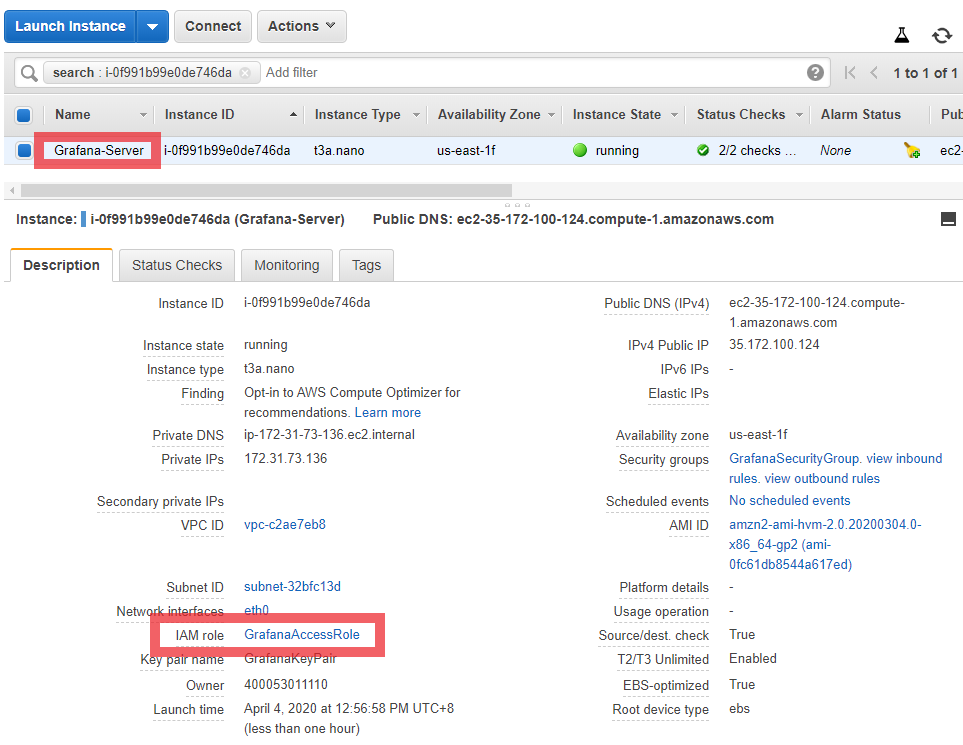
Now that we have attached the IAM Role to the EC2 Instance, we need to add the CloudWatch Data Source to our Grafana Settings.
Adding CloudWatch Data Source
Login to Grafana.
Click on Configuration >> Data Sources.
Click on Add data source.
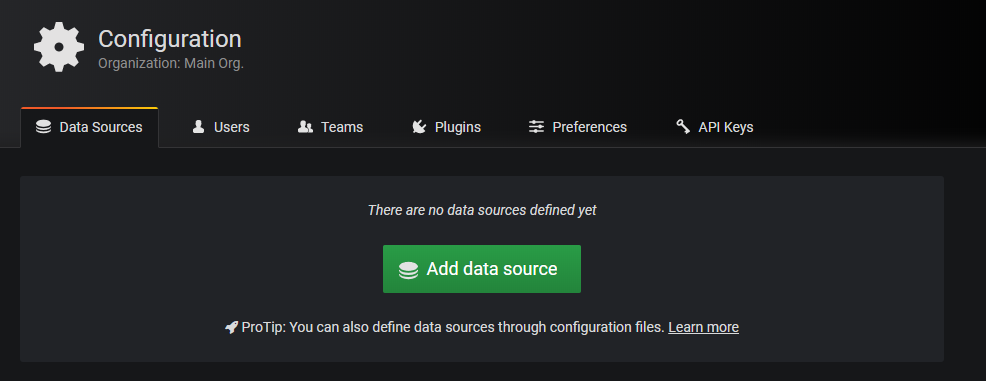
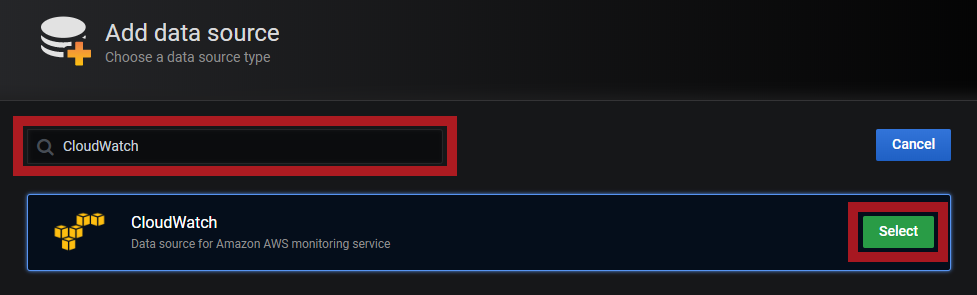
Search for CloudWatch and click Select.
On Data Sources / CloudWatch settings, modify the Name and Default Region. Then click Save & Test.
Leave Auth Provider and Custom Metrics blank.
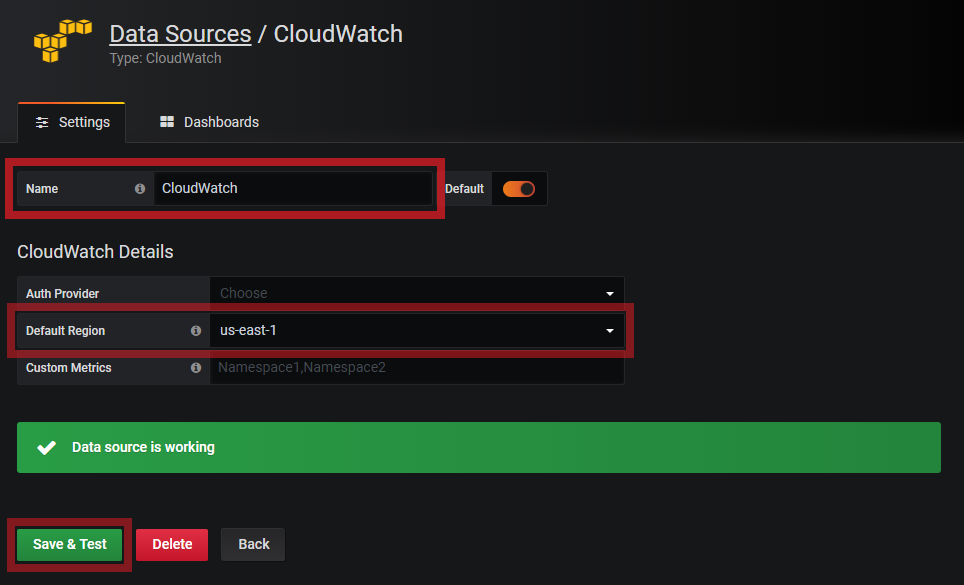
When there is a status that says Data source is working, that shows that Grafana is able to access CloudWatch via the IAM Role.
Note: You can also use the following Auth Provider to access CloudWatch via IAM Role.
Auth Provider: Access & secret key
Leave Access Key ID and Secret Access Key blank. This will use the IAM Role.
Auth Provider: Credentials file
Do not create an AWS Credentials File. This will access CloudWatch via the EC2 IAM Role.
Testing CloudWatch Data Source
To test Grafana accessing CloudWatch via the EC2 IAM Role, create a new Dashboard.
Set the following properties.
| Region | default |
| Namespace | AWS/EC2 |
| Metric Name | CPUUtilization |
| Stats | Average |
| Dimensions | InstandId = <Instance ID of your Grafana Server> |
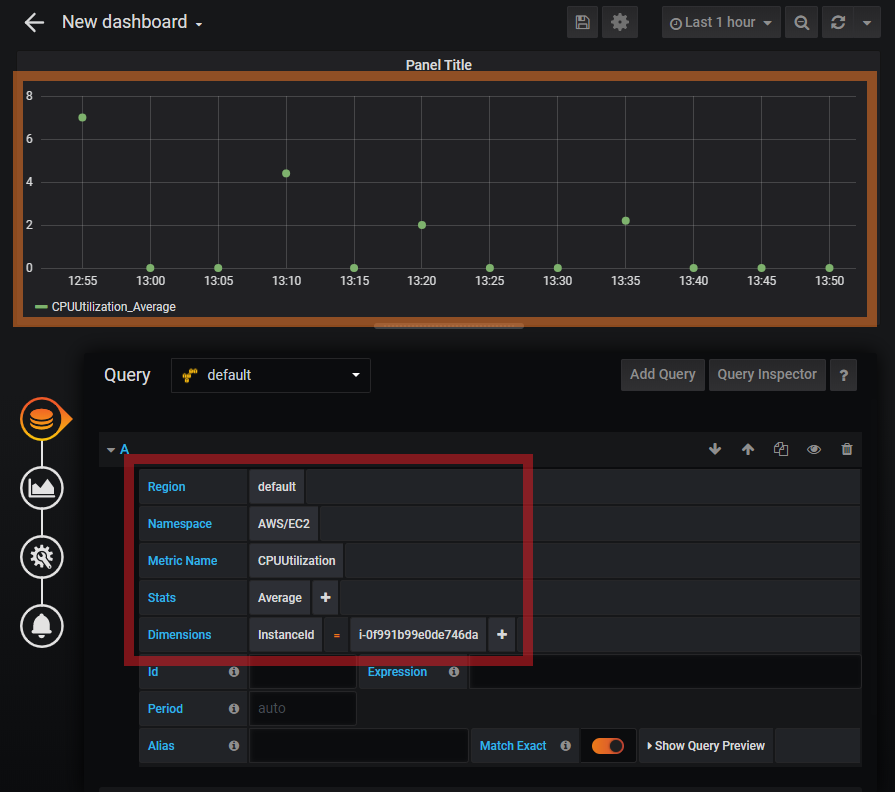
When you see green dots on the Graph, then it means that Grafana Server is able to successfully access CloudWatch via the attached IAM Role of the EC2 Instance.
Note: I adjusted the Graph above to 1 hour duration and Draw Modes: Points with Point Radius of 3 for the green dots to be easily viewed.
If you have questions or encounter an error let me know via the comments below.
Thank you Thank you Thank you sooooo much. This helped me solve my issue for cross account cloudwatch access to grafana.