A headless setup is when your Raspberry Pi is turned on without a monitor.
The display is not needed usually, especially if your access is only via SSH. The issue would be if you connect via VNC Viewer, the display will look like this.
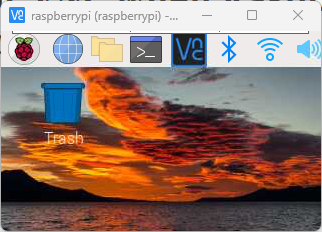
The icons are too big but the screen is too small.
What’s happening here is that Raspberry Pi will use a very small screen resolution when it is not connected to a monitor. So when you connect via VNC Viewer, VNC will get the same small screen resolution.
To solve this, we need to change the default headless screen resolution of the Raspberry Pi. You can follow the instructions below to set this.